Technology can be complicated. Sometimes those of us in the community can make things more complicated. Perhaps unnecessarily so. In my work teaching graduate students in architecture at SMU, I am always coaching them that complexity is not a feature to be designed in, rather it is to be avoided. Simplicity and elegance go a long way towards creating systems, architectures, and businesses that are robust and will endure. Life and technology are complicated enough.

This is particularly true for the burgeoning field of cybersecurity, a hot topic for almost every company today. Cybersecurity and the constantly evolving threats from organized crime and foreign governments are a pervasive concern. Insurer estimates for damages from attacks are that direct and indirect costs will exceed $400 billion this year. As I write this,
- Under Armour is announcing that more than 150 million user accounts have been breached, compromising user information and damaging the company’s reputation.
- Another 5 million payment cards have been taken from Saks and Lord & Taylor stores.
In these scenarios, it may be attractive to want to buy a technology “solution” – which often involves a complicated, time consuming technology platform. This is because quick fix solutions that are complex sell better than a disciplined, prioritized approach.
Edsger W. Dijkstra, the noted Computer Scientist and Physicist, said it this way: “Simplicity is a great virtue but it requires hard work to achieve it and education to appreciate it. And to make matters worse, complexity sells better.” Is there a better way to understand, prioritize, and invest in cybersecurity and lower our operational risk?
Taking a Step Back
If we back away from looking at individual cybersecurity incidents, we notice some global characteristics. One is that there are three components of any cybersecurity equation: people, process, and technology.
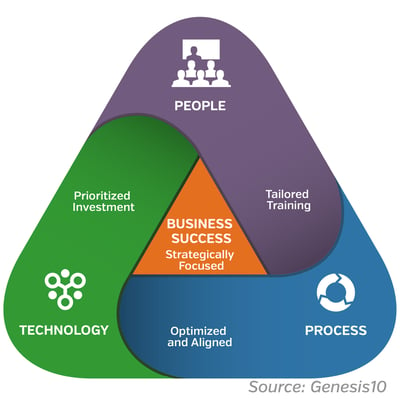
All three must work together well to avoid cybersecurity failures. More important, all three need to be considered in designing an effective cybersecurity system. Despite this, all too often we focus exclusively on technology. What tool can we implement that will insulate us from this risk? How much does it cost, and can we afford it? This is a shortsighted and costly approach, and it does not work. Let’s look a bit more at each of these three areas. Perhaps doing so will bring some helpful perspective.
People and Process, then Technology
In terms of people, the Harvard Business Review notes the following: “the reality is that no matter the size or the scope of a breach, usually it’s caused by an action, or failure, of someone inside the company.” This tells us that the normal failure mode in cyber incidents is not the technology, it is the people and their actions. The study goes on to note: “IBM found that 60% of all attacks were carried out by insiders. Of these attacks, three-quarters involved malicious intent, and one-quarter involved inadvertent actors.”
This tells us a few things. First, despite a tendency to implement technology to solve this problem, it is much bigger. We must start with people, particularly those that are working within our company. Are they aware of the threat? What do they understand about cybersecurity, and how are they trained? How do they do their work, and what are the steps they take to ensure we are not inadvertently putting our systems at risk? These questions should be addressed by ongoing training and education programs. These should be carefully designed and tailored to the specific organization’s culture and way of working.
This brings us to the next area of focus: process. Processes are actions or steps to achieve a specific business goal. There are several available resources from the U.S. government that bring together best practices that will allow companies to assess whether the way that they are working and their processes involved reinforce cybersecurity, or detract from it. US-CERT, the U.S. Computer Emergency Readiness Team, publishes resources and self-assessment forms designed to bring best practices to organizations wanting to assess their readiness. From a process perspective, they are particularly informative in giving organizations an expert-based perspective on how their processes align with their cybersecurity goals.
Finally, let’s discuss technology. Undoubtedly there are good solutions for many of the common technology challenges in cybersecurity. In terms of technology spending, each company should prioritize its needs and pursue these as a normal cost of doing business. A planned, multiyear approach for systems hardening allows for the tailoring of cybersecurity systems to a company’s most pressing needs. In thinking through what provides the most “bang for the buck,” the patching of a company’s existing systems is critical. By far, the clear majority of cyberattacks take advantage of known software and hardware vulnerabilities. Seventy percent of successful cyberattacks exploit known vulnerabilities having readily available patches. Most companies could have easily prevented a data breach if they’d updated their operating systems and applications.
Organizations with large complex server environments require skilled and dedicated teams to plan, manage, deploy and monitor the application of patches. Since patch management often needs to be conducted during off-hours, scheduling of full-time employees can be inconvenient and burdensome. As we advise and partner with companies on their cybersecurity needs, we have found that implementing an effective patch management program is essential. The discipline that comes from a clear focus on this activity and does not disrupt normal operations is critical to business survival.
The Takeaway
Technology problems do not always need or merit technology solutions. In the clear majority of cybersecurity incidents, technology solutions are at the bottom of the list in terms of effective remediation, and studies consistently reinforce this.
Perhaps we should all step back and consider how to tailor effective cybersecurity programs to meet our specific company’s need. Addressing people, process, and then technology may be our best path forward in an increasingly threat filled cybersecurity world.
Matt McBride blogs regularly for Genesis10. Recently he wrote, The Elephant in the Room: Cybersecurity Threats Persvasive, Yet Opportunities Prevail.
Let's continue the dialogue on technology and talent strategy. Subscribe to the Genesis10 blog.