In the past few months alone, there have been numerous news headlines around massive consumer data breaches:
- Target Now Says 70 Million People Hit in Data Breach (WSJ, January 2014)
- Neiman Marcus Sued Over Customer Credit Card Data Breach (Bloomberg, March 2014)
- U.S. Retailer Michaels Warns of Possible Payment Card Breach (Reuters, January 2014)
- California DMV Investigating Potential Credit Card Breach (WSJ, March 2014)
And these are just a few. Even if personally unaffected by recent cybercrime instances, it’s an excellent bet that, no matter where you reside in the business value chain, you are feeling the effects of these stories (or soon will be) as they cascade from consumer retailers, financial services companies and government regulators down throughout business value chains while also spilling over into such areas as cloud hosting providers, data storage, social media and education. What each has in common is that they are uniquely interconnected by their business value chains and handle huge quantities of sensitive digital information.
In Five Megatrends Driving the Rise in US Domestic Outsourcing, we observed that government regulators across several major industry segments are evolving supplier risk-management requirements for the industries they oversee. In particular two industries appear to be at the forefront: financial services and healthcare. Regulators such as the Office of the Comptroller of the Currency (OCC) are increasingly:
- Emphasizing procurement and supplier management practices that include greater due diligence in supplier selection.
- Stepping up scrutiny to ensure that risk-related processes are commensurate with levels of exposure and complexity in supplier relationships and/or work being outsourced to service providers.
- Looking for evidence of rigorous control requirements wherever access to data and risk is being shifted via outsourcing, contingent workforce or other remote/distributed work setups.
From a talent management perspective, we are seeing a rise in both the rigor and levels of controls required by our clients across all Genesis10 service lines, particularly domestic outsourcing via delivery centers, managed services and management consulting but we expect that these requirements will also be extended to staff supplementation services.
Beyond the push from regulators, risk-savvy business leaders are pursuing their own rigorous initiatives to identify and mitigate risks, often requiring suppliers and service providers to maintain robust sets of controls on employment practices, physical security, environmental controls, information security, change management and back up. The controls address a broad array of factors, including but not limited to: hiring practices, employee on- and off-boarding procedures, visitor access management, intrusion detection, security training, logical access to systems & applications, and so much more.
Suppliers and service companies for their part are increasingly pursuing rigorous third-party testing and certifications to various control standards. They do this in order to:
- Exude confidence in their controls and extend confidence to their customers that effective controls have been implemented to safeguard their data.
- Provide independent verification that business objectives are not being compromised.
- Demonstrate committed investment, maturity, rigor and differentiation in the marketplace.
- Alleviate costs and time burdens that inevitably accompany proliferation of control requirements, audits and inspections throughout their business value chains.
The upshot for talent strategists is that choosing service providers to fulfill contingent workforce requirements will and must be conducted increasingly through risk- and control-sensitive lenses. They must also be fine tuned to a company’s position in the overall business value and risk chain. Corporate procurement, treasury and security personnel will become increasingly involved in vetting and selecting contingent workforce service providers.
To share our experiences and to help inform talent strategists on matters of physical and logical environmental controls and security, we sat down recently for an in-depth Q&A with Raja Paranjothi, Senior Manager of Business & Technology Risk Services with Mayer Hoffman McCann P.C. (MHM). Paranjothi’s job is to provide strategic risk advice and assist services companies in evaluating, strengthening and maturing their internal control environment including logical and physical controls. Part 1 of our Q&A looks at the larger business context and value-chain implications.
NOTE: While our discussion is focused on talent management, the same concepts extend to businesses all along the value chain. Control implications will vary based on services provided, where data resides and companies’ risk appetites.
Q: Aside from the pressure coming from regulators, what is motivating companies to focus more on managing business and technology risk?
The biggest drivers are technology and data. Every day there is more sensitive data and content being generated that just hangs out there on the Internet and in the Cloud. There is personal data – social security numbers, bank & credit card account numbers, pin numbers, healthcare and educational records. There are massive quantities of business transaction data. And, as more people and businesses migrate to cloud hosting and data storage services, there are countless instances of remotely hosted documents, files and so much other content that can pose serious risks if it falls into the wrong hands. All of this serves ultimately as a huge source of risk exposure for companies both up and down the business value chain.
Where, in the past, companies did not always view data from a risk perspective, every few days there seems to be a big news story focusing more attention on data security. As more companies migrate work to the Cloud and employ distributed workforce models, and as consumers get more educated about the importance of protecting their data, I believe we will continue to see more proactive emphasis on Service Organization Controls (SOC) or similar compliance reporting.
Q: Can you give us an example of how risk exposure and compliance reporting cascades through a business value chain?
There is definitely a domino effect when work and data move outside a business environment. Risks and needs for controls cascade both up- and downstream in business value chains - to customers and on to their customers and also to suppliers and down their suppliers.
So, for example, we have a client in Baltimore that provides insurance for bank loans. They host their data at a small center in Wichita, Kansas, but they purchase the hosting services through a reseller who provides managed services to the client. The data center does not have a SOC report and nor does the reseller, so the insurance company needs both to obtain SOC reports so it can continue to serve the bank. The control requirements cascade from the bank to the insurance company, to the reseller, to the physical host, which is the value-chain effect. That tiny data center in Wichita needs to invest in having its own rigorous SOC report if it wants to remain in that line of business. In this example, the host provider would be the sub-service organization and they were ‘carved out’ or in other words scoped out the sub-service organization placing the responsibility to manage their respective controls with the data center and the managed services provider through their own SOC report.
Q: You mention SOC reporting. Can you give us a quick overview of what that is and the scope of the controls it covers?
It used to be called SAS 70 until a few years ago when the American Institute of Certified Public Accounts (AICPA) changed the name to Service Organization Controls or SOC (pronounced ‘sock’) report. A SOC report can apply to any type of organization that provides services to its clients. Payroll processors are a good example of the kinds of companies that would proactively obtain SOC reports because they affect the financial reporting of their clients and handle lots of sensitive information such as social security and bank account numbers. They would hire a CPA firm to assess their internal control environment and provide an opinion in the form of a SOC report. The SOC report must be done by a third-party CPA firm and can be anywhere from 30 to 100 pages or longer, depending on the size and complexity of the service organization being tested. The report would detail every control they use in processing a payroll and is something they would give to customers or potential customers to create a sense of comfort that they have controls in place that have been tested and validated by an expert third party.
Q: Are there laws or regulations requiring SOC reporting in certain industries or is it always voluntary?
There are no laws or specific regulations around this. It is essentially customer and client driven. Having a SOC report by a reputable accounting firm can get you in the door of some very large customers. In fact, many of our clients who are service providers use their SOC reports as marketing tools and differentiators. You may notice some companies will place badges or logos on their websites stating that they have SOC reports in place. It is especially important to have a SOC report if you want to do business with financial services companies who are under pressure from both consumers and regulators to mitigate risks.
Q: So, what exactly does it mean to have a SOC report? What does it say essentially about a service provider in terms of their control environment?
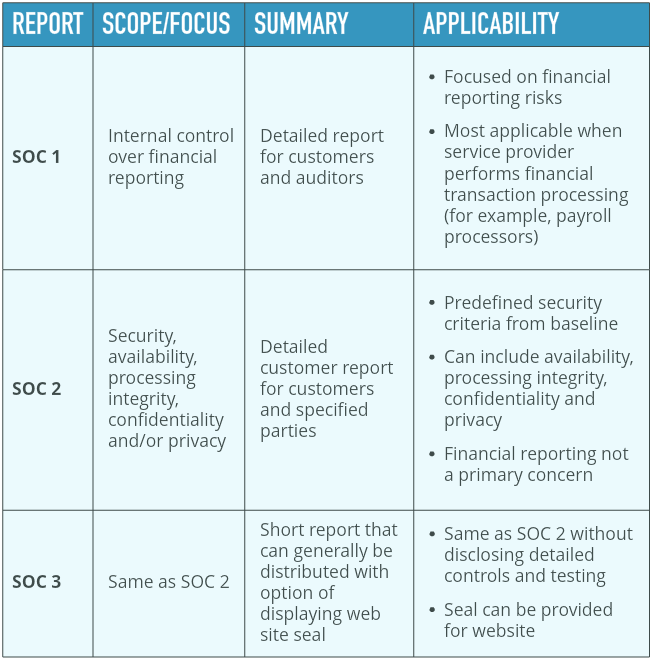
A SOC report follows the Statement on Standards for Attestation Engagements No. 16 or SSAE 16 standard, which is set forth by the AICPA. There are three levels of reporting, SOC 1, 2 and 3. The SOC 1 follows the SSAE 16 standard while SOC 2 and 3 follow the trust principles and criteria, which is significantly different. SOC 1 is really for companies that can have financial impacts on their clients’ financial reporting. So, for example, a payroll company would do SOC 1 because they impact the financial reporting of their clients.
A SOC 2, technically speaking, is for any other service business that does not have direct impact on client financial reporting. Good examples are data centers or Cloud providers. And, while you can argue that Cloud providers can have financial impacts on their clients (in fact, some of the Cloud providers we test choose SOC 1), most in these categories will go with SOC 2, which follows the trust principles of security (physical and logical), availability of networks, applications and so forth; processing integrity, privacy and confidentiality.
SOC 3 is the same as SOC 2 but there is no tangible report. Essentially, a SOC 3 company will show a seal on its website. And, while a SOC 3 represents the same level of controls testing as SOC 2, it is less expensive because the auditor does not write a report. Most companies want the report, so we don’t see a lot of demand for SOC 3.
SOURCE: MAYER HOFFMAN MCCANN P.C.
Stay tuned for Part 2 in our Q&A in which we look in greater detail at how talent strategists can integrate physical, environmental and logical control requirements into their supplier management practices. The controls can be incorporated as part of a comprehensive due diligence effort to evaluate new suppliers, heighten capabilities of existing suppliers or to rationalize your current supplier bases in order to further manage and mitigate risk within the business value chain.














